1)
Create 3 namespaces, 3 veth pairs and a linux bridge
create_3_namespaces_and_1_bridge()
{
echo "Creating namespace and bridge......"
###Create 3 Namespaces
sudo ip netns add ns1
sudo ip netns add ns2
sudo ip netns add ns3
###Create Bridge
sudo brctl addbr br-test
sudo brctl stp br-test off
sudo ip link set dev br-test up
###Create veth pairs tap1---br-tap1
sudo ip link add tap1 type veth peer name br-tap1
#Move tap1 to ns1
sudo ip link set tap1 netns ns1
#Add br-tap1 to bridge br-test
sudo brctl addif br-test br-tap1
#UP tap1
sudo ip netns exec ns1 ip link set dev tap1 up
#UP br-tap1
sudo ip link set dev br-tap1 up
###Create veth pairs tap2---br-tap2
sudo ip link add tap2 type veth peer name br-tap2
#Move tap2 to ns2
sudo ip link set tap2 netns ns2
#Add br-tap2 to bridge br-test
sudo brctl addif br-test br-tap2
#UP tap2
sudo ip netns exec ns2 ip link set dev tap2 up
#UP br-tap2
sudo ip link set dev br-tap2 up
###Create veth pairs tap3---br-tap3
sudo ip link add tap3 type veth peer name br-tap3
#Move tap3 to ns3
sudo ip link set tap3 netns ns3
#Add br-tap3 to bridge br-test
sudo brctl addif br-test br-tap3
#UP tap3
sudo ip netns exec ns3 ip link set dev tap3 up
#UP br-tap3
sudo ip link set dev br-tap3 up
###Assign IP
#Assign IP to tap1
sudo ip netns exec ns1 ip addr add 10.1.1.4/24 dev tap1
#Assign IP to tap2
sudo ip netns exec ns2 ip addr add 10.1.1.5/24 dev tap2
#Assign IP to tap3
sudo ip netns exec ns3 ip addr add 10.1.1.6/24 dev tap3
###Test Ping
sudo ip netns exec ns1 ping 10.1.1.5 -c 1
if [ $? -eq 0 ]; then
echo "Ping working from ns1 (10.1.1.4) to ns2 (10.1.1.5)"
echo "Created namespace and bridge......"
else
echo "Failed to Create namespace and bridge......"
fi
}
delete_3_namespaces_and_1_bridge()
{
echo "Deleting namespace and bridge......"
sudo ip netns del ns1
sudo ip netns del ns2
sudo ip netns del ns3
sudo ip link set dev br-test down
sudo brctl delbr br-test
if [ $? -eq 0 ]; then
echo "Deleted namespace and bridge......"
else
echo "Failed to delete namespace and bridge......"
fi
}
create_3_namespaces_and_1_bridge
#delete_3_namespaces_and_1_bridge
* We don't need to add IP to the linux bridge.Bridge will act as a switch and broadcast the APR packets and make entries into the MAC table in the bridge, we can use the command "brctl showmacs
" to see this table.
* When you ping from "tap1" in namespace "ns1" to "tap2" in namespace "ns2", "tap1" first send a ARP broadcast packet and and that packet will get received by bridge "br-test" via the interface "br-tap1", then the bridge will broadcast that ARP packet to all interfaces connected to that bridge, So the interface "tap2" get that packest via the interface "br-tap2", "tap1" will indentify that the destination IP is belongs to that interface and send a ARP ACK packet back to the interface "tap1". Once the "tap1" get that ARP ACK packet, that will populate the ARP table in the namespace "ns1" with IP and MAC entry. Then the ping (ICMP) packest are send from "tap1" to "tap2" based on the ARP table in the namespace "ns1", MAC table in the bridge "br-test" and ARP table in the "ns2".
2)
Capture ICMP and ARP packets from all veth interfaces
2a)
Capture ICMP and ARP packets from interface tap1 and br-tap1
#sudo ip netns exec ns1 tshark -i tap1 -f "icmp or arp"
#sudo tshark -i br-tap1 -f "icmp or arp"
2b)
Capture ICMP and ARP packets from interface tap2 and br-tap2
#sudo ip netns exec ns2 tshark -i tap2 -f "icmp or arp"
#sudo tshark -i br-tap2 -f "icmp or arp"
2c)
Capture ICMP and ARP packets from interface tap3 and br-tap3
#sudo ip netns exec ns3 tshark -i tap3 -f "icmp or arp"
#sudo tshark -i br-tap3 -f "icmp or arp"
3)
List ARP table of namespace ns1, ns2 and ns3 and Clear it
3a)
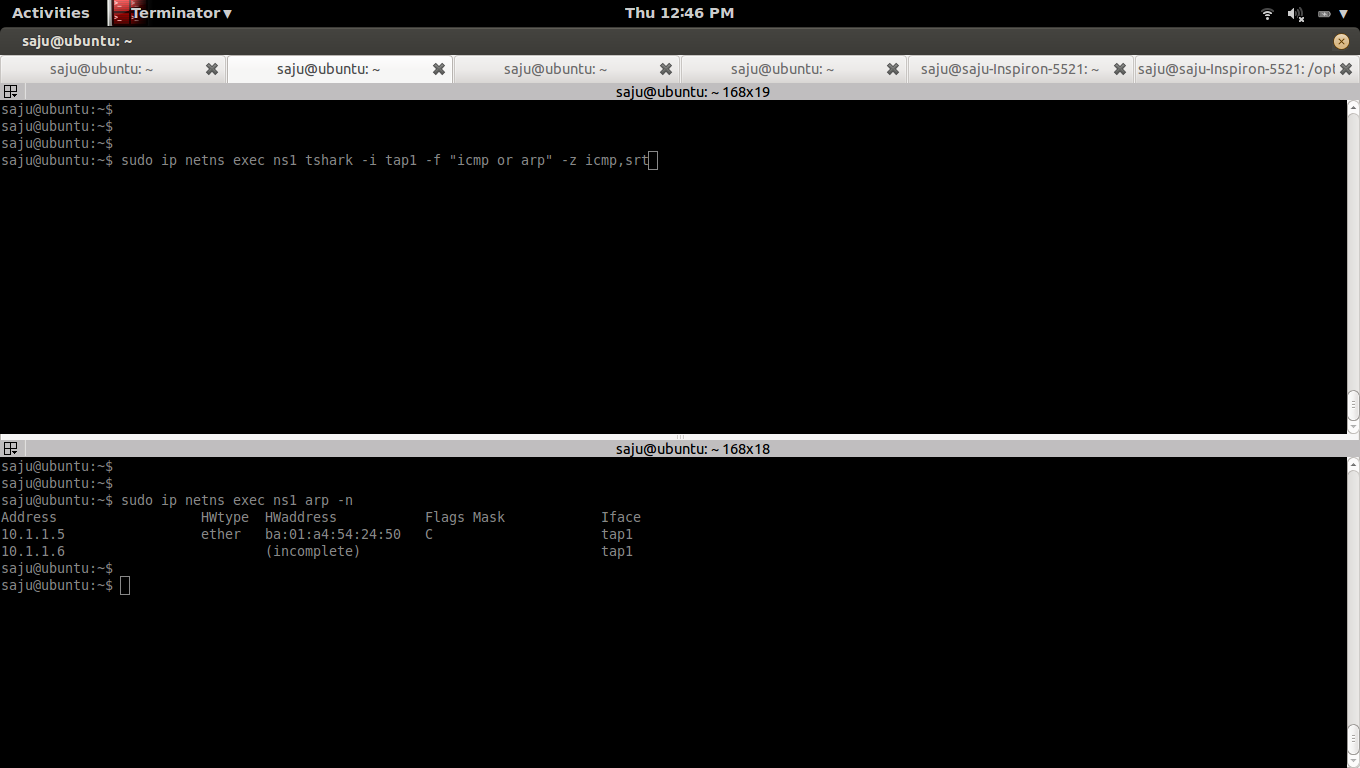
List ARP table
#sudo ip netns exec ns1 arp -n
Clear ARP table
#sudo ip netns exec ns1 arp -d
3b)
#sudo ip netns exec ns2 arp -n
#sudo ip netns exec ns2 arp -d
3c)
#sudo ip netns exec ns3 arp -n
#sudo ip netns exec ns3 arp -d
4)
Ping from ns1 (10.1.1.4) to ns2 (10.1.1.5)
#sudo ip netns exec ns1 ping 10.1.1.5
5)
5a)
5a,a)
Capture ICMP and ARP packets from interface tap1 and br-tap1
#sudo ip netns exec ns1 tshark -i tap1 -f "icmp or arp"
1 0.000000 be:bb:98:99:fe:b1 -> Broadcast ARP 42 Who has 10.1.1.5? Tell 10.1.1.4
2 0.000103 ba:01:a4:54:24:50 -> be:bb:98:99:fe:b1 ARP 42 10.1.1.5 is at ba:01:a4:54:24:50
3 0.000106 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=1/256, ttl=64
4 0.000158 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=1/256, ttl=64 (request in 3)
4 5 1.000704 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=2/512, ttl=64
5 6 1.000865 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=2/512, ttl=64 (request in 5)
6 7 2.003246 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=3/768, ttl=64
7 8 2.003495 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=3/768, ttl=64 (request in 7)
8 9 3.004683 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=4/1024, ttl=64
9 10 3.004873 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=4/1024, ttl=64 (request in 9)
10 11 4.006729 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=5/1280, ttl=64
11 12 4.006921 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=5/1280, ttl=64 (request in 11)
12 13 5.008408 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=6/1536, ttl=64
13 14 5.008551 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=6/1536, ttl=64 (request in 13)
15 5.008641 ba:01:a4:54:24:50 -> be:bb:98:99:fe:b1 ARP 42 Who has 10.1.1.4? Tell 10.1.1.5
16 5.008654 be:bb:98:99:fe:b1 -> ba:01:a4:54:24:50 ARP 42 10.1.1.4 is at be:bb:98:99:fe:b1
16 17 6.009508 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=7/1792, ttl=64
18 6.009641 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=7/1792, ttl=64 (request in 17)
18 19 7.016597 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=8/2048, ttl=64
20 7.016719 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=8/2048, ttl=64 (request in 19)
Notes:
* Interface "tap1"(be:bb:98:99:fe:b1) first Broadcast (send) an ARP packet to find MAC address associated with the IP 10.1.1.5. You can see it in line-1. You can see that, in that packet source MAC address is the MAC address of interface "tap1" and destination MAC address is None(Broadcast).
* In line-2, you can see that an ARP packet comes to Interface "tap1"(be:bb:98:99:fe:b1) from Interface "tap2"(ba:01:a4:54:24:50) and tells that the IP:10.1.1.5 is belongs to the interface "tap2"(ba:01:a4:54:24:50).You can see that, in that packet source MAC address is the MAC address of interface "tap2" and destination MAC address of interface "tap1".
* At this point, ARP table in the namespace "ns1" get populated with an entry of IP and MAC map, IP:10.1.1.5 and MAC:ba:01:a4:54:24:50. You can list ARP table in the namespace "ns1" with following command.
#sudo ip netns exec ns1 arp -n
Address HWtype HWaddress Flags Mask Iface
10.1.1.5 ether ba:01:a4:54:24:50 C tap1
* In line-3, send ICMP request packet.In that packet source IP is 10.1.1.4 and destination IP is 10.1.1.5
* In line-4, receive ICMP reply packet.In that packet source IP is 10.1.1.5 and destination IP is 10.1.1.4
* In line-15, receive ARP request packet from interface "tap2"(ba:01:a4:54:24:50) and asking that, is the IP:10.1.1.4 belongs to the interface "tap1", if yes, send a ARP reply packet.In that packet source MAC is "tap2"(ba:01:a4:54:24:50) and destination MAC is "tap1"(be:bb:98:99:fe:b1)
* In line-16, send ARP reply packet and tells that the IP:10.1.1.4 is associated with interface "tap1"(be:bb:98:99:fe:b1).
* At this point, ARP table in the namespace "ns2" get populated with an entry of IP and MAC map, IP:10.1.1.4 and MAC:be:bb:98:99:fe:b1. You can list ARP table in the namespace "ns2" with following command.
#sudo ip netns exec ns2 arp -n
Address HWtype HWaddress Flags Mask Iface
10.1.1.4 ether be:bb:98:99:fe:b1 C tap2
5a,b)
#sudo tshark -i br-tap1 -f "icmp or arp"
1 0.000000 be:bb:98:99:fe:b1 -> Broadcast ARP 42 Who has 10.1.1.5? Tell 10.1.1.4
2 0.000077 ba:01:a4:54:24:50 -> be:bb:98:99:fe:b1 ARP 42 10.1.1.5 is at ba:01:a4:54:24:50
3 0.000082 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=1/256, ttl=64
4 0.000132 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=1/256, ttl=64 (request in 3)
4 5 1.000699 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=2/512, ttl=64
6 1.000836 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=2/512, ttl=64 (request in 5)
6 7 2.003234 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=3/768, ttl=64
8 2.003465 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=3/768, ttl=64 (request in 7)
8 9 3.004677 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=4/1024, ttl=64
10 3.004823 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=4/1024, ttl=64 (request in 9)
10 11 4.006724 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=5/1280, ttl=64
12 4.006892 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=5/1280, ttl=64 (request in 11)
12 13 5.008405 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=6/1536, ttl=64
14 5.008523 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=6/1536, ttl=64 (request in 13)
15 5.008613 ba:01:a4:54:24:50 -> be:bb:98:99:fe:b1 ARP 42 Who has 10.1.1.4? Tell 10.1.1.5
16 5.008631 be:bb:98:99:fe:b1 -> ba:01:a4:54:24:50 ARP 42 10.1.1.4 is at be:bb:98:99:fe:b1
16 17 6.009503 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=7/1792, ttl=64
18 6.009613 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=7/1792, ttl=64 (request in 17)
18 19 7.016586 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=8/2048, ttl=64
20 7.016691 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=8/2048, ttl=64 (request in 19)
5b)
shows a list of learned MAC addresses for bridge "br-test"
#sudo brctl showmacs br-test
port no mac addr is local? ageing timer
3 66:c3:81:40:76:8c yes 0.00
1 86:1f:a0:72:1c:ea yes 0.00
2 86:d2:d0:1b:af:9e yes 0.00
* 1 --> br-tap1
* 2 --> br-tap2
* 3 --> br-tap3
Notes:
* Bridge "br-test" will broadcast first ARP packet (0.000000 be:bb:98:99:fe:b1 -> Broadcast ARP 42 Who has 10.1.1.5? Tell 10.1.1.4) from the interface "tap1" via "br-tap1" to all other interfaces ("br-tap2" and "br-tap3") attached to the bridge. Please check packets captured from "tap2", "br-tap2" and "tap3", "br-tap3", You can see this ARP packets there.
5c)
5c,a)
Capture ICMP and ARP packets from interface tap2 and br-tap2
#sudo ip netns exec ns2 tshark -i tap2 -f "icmp or arp"
1 0.000000 be:bb:98:99:fe:b1 -> Broadcast ARP 42 Who has 10.1.1.5? Tell 10.1.1.4
2 0.000037 ba:01:a4:54:24:50 -> be:bb:98:99:fe:b1 ARP 42 10.1.1.5 is at ba:01:a4:54:24:50
3 0.000068 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=1/256, ttl=64
4 0.000099 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=1/256, ttl=64 (request in 3)
4 5 1.000731 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=2/512, ttl=64
5 6 1.000789 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=2/512, ttl=64 (request in 5)
6 7 2.003271 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=3/768, ttl=64
7 8 2.003321 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=3/768, ttl=64 (request in 7)
8 9 3.004730 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=4/1024, ttl=64
10 3.004777 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=4/1024, ttl=64 (request in 9)
10 11 4.006775 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=5/1280, ttl=64
12 4.006823 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=5/1280, ttl=64 (request in 11)
12 13 5.008434 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=6/1536, ttl=64
13 14 5.008479 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=6/1536, ttl=64 (request in 13)
15 5.008568 ba:01:a4:54:24:50 -> be:bb:98:99:fe:b1 ARP 42 Who has 10.1.1.4? Tell 10.1.1.5
16 5.008612 be:bb:98:99:fe:b1 -> ba:01:a4:54:24:50 ARP 42 10.1.1.4 is at be:bb:98:99:fe:b1
16 17 6.009529 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=7/1792, ttl=64
18 6.009570 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=7/1792, ttl=64 (request in 17)
18 19 7.016606 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=8/2048, ttl=64
20 7.016647 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=8/2048, ttl=64 (request in 19)
Notes:
* Line-1, interface "tap2"(ba:01:a4:54:24:50) receives a ARP packets which asks "Who has 10.1.1.5? Tell 10.1.1.4"
* Line-2, interface "tap2"(ba:01:a4:54:24:50) sends a ARP reply packet which tells that the IP:10.1.1.5 is ours.
* Line-15, interface "tap2"(ba:01:a4:54:24:50) sends a ARP packets which asks "Who has 10.1.1.4? Tell 10.1.1.5"
* Line-16, interface "tap2"(ba:01:a4:54:24:50) sends a ARP reply packet which tells that the IP:10.1.1.4 is belogs to the interface "tap1"(be:bb:98:99:fe:b1).
* At this point, ARP table in the namespace "ns2" get populated with an entry of IP and MAC map, IP:10.1.1.4 and MAC:be:bb:98:99:fe:b1. You can list ARP table in the namespace "ns2" with following command.
#sudo ip netns exec ns2 arp -n
Address HWtype HWaddress Flags Mask Iface
10.1.1.4 ether be:bb:98:99:fe:b1 C tap2
5c,b)
#sudo tshark -i br-tap2 -f "icmp or arp"
1 0.000000 be:bb:98:99:fe:b1 -> Broadcast ARP 42 Who has 10.1.1.5? Tell 10.1.1.4
1 2 0.000042 ba:01:a4:54:24:50 -> be:bb:98:99:fe:b1 ARP 42 10.1.1.5 is at ba:01:a4:54:24:50
3 0.000071 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=1/256, ttl=64
4 0.000105 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=1/256, ttl=64 (request in 3)
4 5 1.000724 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=2/512, ttl=64
6 1.000797 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=2/512, ttl=64 (request in 5)
6 7 2.003267 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=3/768, ttl=64
8 2.003329 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=3/768, ttl=64 (request in 7)
8 9 3.004703 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=4/1024, ttl=64
9 10 3.004784 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=4/1024, ttl=64 (request in 9)
10 11 4.006770 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=5/1280, ttl=64
11 12 4.006830 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=5/1280, ttl=64 (request in 11)
12 13 5.008430 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=6/1536, ttl=64
13 14 5.008486 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=6/1536, ttl=64 (request in 13)
15 5.008578 ba:01:a4:54:24:50 -> be:bb:98:99:fe:b1 ARP 42 Who has 10.1.1.4? Tell 10.1.1.5
16 5.008614 be:bb:98:99:fe:b1 -> ba:01:a4:54:24:50 ARP 42 10.1.1.4 is at be:bb:98:99:fe:b1
16 17 6.009525 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=7/1792, ttl=64
18 6.009577 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=7/1792, ttl=64 (request in 17)
18 19 7.016606 10.1.1.4 -> 10.1.1.5 ICMP 98 Echo (ping) request id=0x4456, seq=8/2048, ttl=64
20 7.016654 10.1.1.5 -> 10.1.1.4 ICMP 98 Echo (ping) reply id=0x4456, seq=8/2048, ttl=64 (request in 19)
5d)
5d,a)
Capture ICMP and ARP packets from interface tap3 and br-tap3
#sudo ip netns exec ns3 tshark -i tap3 -f "icmp or arp"
1 0.000000 be:bb:98:99:fe:b1 ->
Broadcast ARP 42 Who has 10.1.1.5? Tell 10.1.1.4
Notes:
* Line-1, interface "tap3"(c2:73:bd:3a:bc:65) receives a ARP packet which asks "Who has 10.1.1.5? Tell 10.1.1.4". and no reply packet since the IP:10.1.1.5 doesn't belongs to the interface "tap3"
5d,b)
#sudo tshark -i br-tap3 -f "icmp or arp"
1 0.000000 be:bb:98:99:fe:b1 ->
Broadcast ARP 42 Who has 10.1.1.5? Tell 10.1.1.4
Notes:
* Line-1, interface "br-tap3"(66:c3:81:40:76:8c) receives a ARP packet which asks "Who has 10.1.1.5? Tell 10.1.1.4". and no reply packet since the IP:10.1.1.5 doesn't belongs to the interface "br-tap3"
6)
6a)
Interface Configuration of veth pairs tap1 and br-tap1
#sudo ip netns exec ns1 ifconfig tap1
tap1 Link encap:Ethernet
HWaddr be:bb:98:99:fe:b1
inet addr:10.1.1.4 Bcast:0.0.0.0 Mask:255.255.255.0
inet6 addr: fe80::bcbb:98ff:fe99:feb1/64 Scope:Link
UP BROADCAST
RUNNING MULTICAST MTU:1500 Metric:1
RX packets:58 errors:0 dropped:0 overruns:0 frame:0
TX packets:43 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:4836 (4.8 KB) TX bytes:3630 (3.6 KB)
#ifconfig br-tap1
br-tap1 Link encap:Ethernet
HWaddr 86:1f:a0:72:1c:ea
inet6 addr: fe80::841f:a0ff:fe72:1cea/64 Scope:Link
UP BROADCAST
RUNNING MULTICAST MTU:1500 Metric:1
RX packets:43 errors:0 dropped:0 overruns:0 frame:0
TX packets:58 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:3630 (3.6 KB) TX bytes:4836 (4.8 KB)
6b)
Interface Configuration of veth pairs tap2 and br-tap2
#sudo ip netns exec ns2 ifconfig tap2
tap2 Link encap:Ethernet
HWaddr ba:01:a4:54:24:50
inet addr:10.1.1.5 Bcast:0.0.0.0 Mask:255.255.255.0
inet6 addr: fe80::b801:a4ff:fe54:2450/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:54 errors:0 dropped:0 overruns:0 frame:0
TX packets:35 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:4484 (4.4 KB) TX bytes:3014 (3.0 KB)
#ifconfig br-tap2
br-tap2 Link encap:Ethernet
HWaddr 86:d2:d0:1b:af:9e
inet6 addr: fe80::84d2:d0ff:fe1b:af9e/64 Scope:Link
UP BROADCAST
RUNNING MULTICAST MTU:1500 Metric:1
RX packets:35 errors:0 dropped:0 overruns:0 frame:0
TX packets:54 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:3014 (3.0 KB) TX bytes:4484 (4.4 KB)
6c)
Interface Configuration of veth pairs tap3 and br-tap3
#sudo ip netns exec ns3 ifconfig tap3
tap3 Link encap:Ethernet
HWaddr c2:73:bd:3a:bc:65
inet addr:10.1.1.6 Bcast:0.0.0.0 Mask:255.255.255.0
inet6 addr: fe80::c073:bdff:fe3a:bc65/64 Scope:Link
UP BROADCAST
RUNNING MULTICAST MTU:1500 Metric:1
RX packets:33 errors:0 dropped:0 overruns:0 frame:0
TX packets:15 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:2566 (2.5 KB) TX bytes:1222 (1.2 KB)
#ifconfig br-tap3
br-tap3 Link encap:Ethernet
HWaddr 66:c3:81:40:76:8c
inet6 addr: fe80::64c3:81ff:fe40:768c/64 Scope:Link
UP BROADCAST
RUNNING MULTICAST MTU:1500 Metric:1
RX packets:15 errors:0 dropped:0 overruns:0 frame:0
TX packets:33 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:1222 (1.2 KB) TX bytes:2566 (2.5 KB)
6d)
Interface Configuration of bridge br-test
#ifconfig br-test
br-test Link encap:Ethernet
HWaddr 66:c3:81:40:76:8c
inet6 addr: fe80::1ca2:7eff:fe1e:51a2/64 Scope:Link
UP BROADCAST
RUNNING MULTICAST MTU:1500 Metric:1
RX packets:24 errors:0 dropped:0 overruns:0 frame:0
TX packets:8 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:1476 (1.4 KB) TX bytes:648 (648.0 B)